Address
Australia, Singapore, and USA
Address
Australia, Singapore, and USA

Learn how to share files securely with this practical guide. We cover encryption, secure platforms, and strategies to protect your data across global teams.
Using tools like end-to-end encryption and time-limited links is the fastest, most effective way to share files securely with your team, whether they’re across the hall or across the globe. By sending password-protected links that expire, you shut the door on unauthorized access before it can even happen. This isn’t just good practice; it’s the core of any modern file-sharing routine, especially for businesses with an international reach.
In today’s world of global, remote teams, sloppy file-sharing habits are no longer just a bad habit—they’re a serious business risk.
Think about it. Shooting over a sensitive contract using a personal email account or stashing proprietary data in a consumer-grade cloud service is practically an open invitation for a breach. This is especially true when operating across borders, where different data privacy laws and security norms create a complex web of risks.

When you lock down your file sharing, the benefits are immediate and obvious:
Data breaches aren’t just about lost files; the stakes are incredibly high, and the consequences can be devastating.
The numbers are staggering. According to recent projections, the global cost of cybercrime is on track to hit $10.5 trillion by 2025. The average cost of a single breach has already climbed to $4.88 million, and incidents involving remote work tack on an extra $173,074 to the bill. You can dig into these jaw-dropping stats over at Cobalt IO.
These aren’t just figures on a page. The financial fallout often blows past what most companies have set aside for IT emergencies, and the damage to your reputation can slam doors shut with clients and partners for good, hindering your international growth.
“Secure sharing isn’t an extra step; it’s the core of operational resilience. For global companies, it’s also the foundation of international trust and compliance.” — Kara Liu, Cybersecurity Consultant
How you handle data directly impacts your brand’s credibility and your ability to meet compliance standards in multiple regions. Mastering secure file sharing is a direct investment in building trust and slashing risk on a global scale.
If you do business internationally, you know that regulations like GDPR in Europe, CCPA in California, and others demand strict controls over how data is handled. This isn’t optional, and it’s a key part of any successful international keyword strategy that aims to attract customers in these markets.
A crucial piece of this is the audit trail. These logs are your proof of compliance, showing every single interaction with a document.
An audit trail helps you:
For teams scattered across different time zones, features like expiring links are invaluable. They automatically shrink the window of exposure, while password protection and the ability to revoke a link on demand stop unintended downloads in their tracks. This level of control is essential for conversion optimization per region, as local customers are more likely to trust businesses that demonstrate robust data governance.
Secure file sharing quickly becomes a core competency that separates the best global teams from the rest. Clients and partners are far more likely to trust providers who can demonstrate solid data safety practices that align with international standards.
This builds what we call operational resilience—the ability to bounce back quickly when threats inevitably appear.
When you embrace these practices, you transform file sharing from a point of vulnerability into a source of strength. It’s a core skill you can master today with the right approach and tools.
For teams working across borders, the challenges multiply. You’re dealing with different server locations, data residency laws, and the need to manage localized content for various regions.
Best practices for global teams include:
Prioritizing secure file sharing delivers an immediate return on investment, primarily by cutting down the massive costs associated with a potential data breach and building the trust needed for global expansion.
Figuring out the right way to share files securely isn’t about finding one magical “best” tool. It’s about matching the solution to your specific situation. The needs of a freelancer sending a single contract are worlds apart from a multinational corporation juggling project files across several continents.
Your decision should really come down to a balance of three things: security, ease of use, and scalability. This is especially true when you’re working with international teams, where you have to think about things like data residency laws (hello, GDPR) and making sure the tool is accessible even for your least tech-savvy team members. A seamless user experience is one of the content types that drive global conversions.
When you need to send files securely, you’re generally looking at three main buckets. Each one is built for a different job and comes with its own level of control and technical know-how.
You absolutely need to understand the encryption that powers these services. This visual breaks down the two main types you’ll run into.
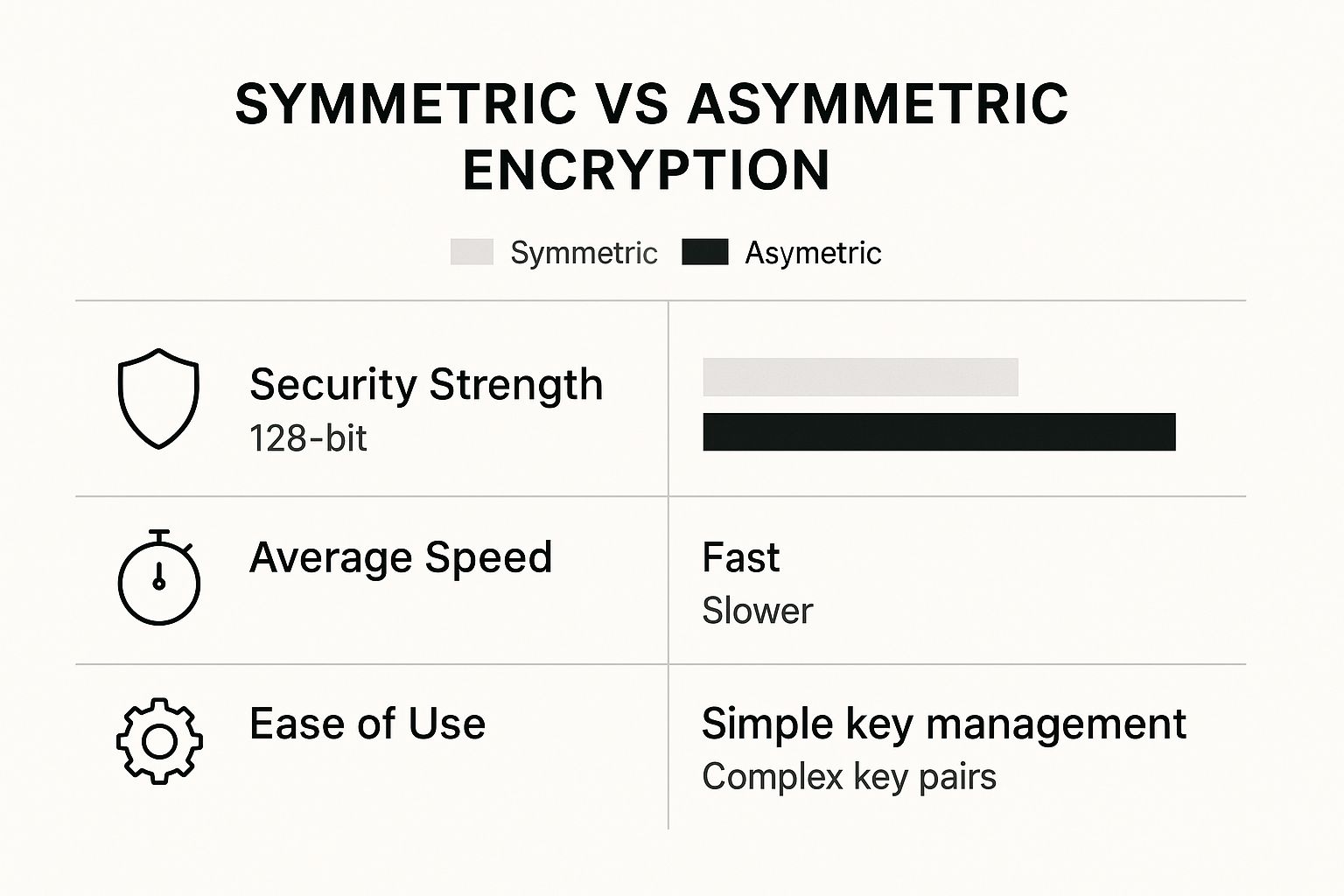
The big takeaway here is that asymmetric encryption offers much stronger protection, which is vital when you’re sending sensitive data to outside parties. In contrast, symmetric encryption is all about speed, making it great for files being used within a trusted system.
So, how do you actually choose? Start by looking at how your team works. A design agency in London sharing huge video files with a client in Tokyo needs speed and simplicity above all else. For them, an end-to-end encrypted cloud platform is a perfect fit.
On the other hand, a financial firm that needs to automate daily report transfers between its New York and Frankfurt offices would get far more value from a dedicated SFTP solution. The demand for these kinds of powerful, specialized solutions is growing for a reason.
The global Secure File Transfer market is expanding fast, projected to jump from $2.35 billion in 2024 to $3.63 billion by 2029. This growth is being fueled by a sharp rise in cybersecurity threats and the sheer volume of data created by international business. If you’re interested, you can explore the full market report on The Business Research Company.
This trend really highlights the importance of picking a solution that can handle not just what you need today, but what you’ll need tomorrow as your international footprint grows.
To help you weigh the pros and cons, this table breaks down the common methods.
This table compares key features, best use cases, and security levels of common file sharing methods to help you choose the right one for your needs.
| Method | Primary Security Feature | Best For | Global Scalability |
|---|---|---|---|
| Encrypted Cloud Storage | End-to-end & at-rest encryption | Collaborative projects, sharing with non-technical users, everyday use | High; designed for global access with regional data centers |
| SFTP Services | Encrypted transfer channel (SSH) | Automated, high-volume, or system-to-system transfers | High; requires technical setup at each endpoint |
| Secure Email Platforms | Encrypted messages and attachments | One-off transfers of small to medium-sized files to specific recipients | Moderate; can be limited by file size and recipient setup |
Choosing the right tool ultimately comes down to your unique workflow and risk profile. For most businesses needing a blend of security and usability for international collaboration, a dedicated cloud storage platform often hits the sweet spot.
A platform built with a zero-knowledge architecture—where not even the service provider can access your encryption keys—gives you the highest possible level of privacy and control. For a much deeper look at the nuts and bolts, check out our guide on how to get a truly secure online file transfer.
In the end, the best choice is the one that empowers your team to work efficiently without ever having to compromise on security, no matter where in the world they are.

If you really want to master secure file sharing, you need to get familiar with the pillars that hold the whole thing up. These aren’t just technical buzzwords; they’re the concepts that give you genuine control over your data. By truly understanding these four principles, you can turn abstract security theory into concrete, everyday habits that protect your work, especially when collaborating across borders.
Think of them as a layered defense, where each principle works with the others to build a strong barrier against data leaks and prying eyes.
End-to-end encryption (E2EE) is the absolute bedrock of modern data security. Imagine you write a sensitive letter, lock it in a steel box, and send the only key directly to your recipient. No one else—not the courier, not the platform you used to send it, not even a hacker who intercepts the package—can get inside.
That’s exactly how E2EE operates. Your file gets scrambled and locked on your device before it ever touches the internet. It only gets unlocked once it arrives safely on the recipient’s device. This ensures your data stays completely unreadable and private for its entire journey.
Key Takeaway: End-to-end encryption means even the service provider you’re using can’t see your files. This is the highest level of privacy you can get and should be non-negotiable for sensitive or proprietary information.
For any business with a global footprint, this is a must. It guarantees that the files shared between your Paris office and your Tokyo team are completely shielded from snooping, no matter which networks they cross. This technical assurance is crucial for backlink building in target regions, as reputable international sites will only link to trustworthy resources.
Encrypting a file is a great start, but it’s not enough. You also need to control precisely what the person on the other end can do with it. That’s where access control comes in. It’s the digital version of a building’s security pass, giving different levels of clearance to different people.
Think about a marketing agency sending localized content for a campaign proposal to a client. The client obviously needs to see the document, but you certainly don’t want them editing it or, worse, forwarding it to a competitor.
With granular access controls, you can set specific permissions:
Setting these roles prevents both accidental mix-ups and deliberate leaks, giving you total command over your intellectual property. Our guide on secure document sharing goes much deeper into how to set these permissions up the right way.
Shared links are incredibly convenient, but a public, permanent link is a security problem waiting to happen. To fix this common weak spot, you need to use two simple but incredibly effective tools: password protection and link expirations.
First, adding a password to a shared link creates an essential second hurdle. Even if the link gets accidentally forwarded or somehow leaks, it’s useless without the password—which you should always share through a different channel, like a quick text message or phone call.
Setting an expiration date is just as vital. For example, a freelancer can send a design proof to a client with a link that automatically dies after 48 hours. This simple action dramatically shrinks the window of opportunity for someone to find and misuse that link long after the project is done. It makes sure old links don’t become forgotten backdoors to your data.
Finally, a complete audit trail gives you the accountability you need for compliance and security monitoring. An audit trail is basically an unchangeable diary that logs every single action taken on a file: who opened it, when they opened it, what they did (view, download, edit), and even where they did it from.
For a legal team managing compliance across Europe and North America, this isn’t just a nice feature to have; it’s a hard requirement for proving GDPR and CCPA compliance. If a regulator ever comes knocking, that audit trail is your definitive proof of responsible data handling. It also serves as an early-warning system, helping you spot weird activity—like multiple downloads from an unrecognized country—that could signal a security breach in progress.
Even with the best security tools in place, it’s the small, everyday habits that can quietly punch holes in your defenses. Learning how to share files securely, especially when your team is spread across the globe, starts with spotting these subtle mistakes. These aren’t dramatic system failures; they’re the relatable, all-too-common shortcuts that weaken your security from the inside out.
One of the most frequent—and riskiest—behaviors is mixing personal and professional accounts. It feels quick and harmless to just send a work file from your personal Google Drive, but doing so pushes sensitive company data completely outside of your organization’s control and security perimeter.
The temptation to use familiar tools is strong, and it often leads people to take shortcuts they know they shouldn’t. The data on this is pretty eye-opening. A recent study found that a staggering 56% of employees in the U.S. have used personal file-sharing services like Dropbox for work purposes, often flying in the face of company policy. On top of that, 63% admit to using personal email for work-related file transfers, with most doing so every single month. If you’re curious about the numbers, you can explore more 2025 file transfer statistics to see how these habits magnify breach risks.
When this happens, all the carefully built security measures your company relies on—like audit trails and access controls—are completely bypassed. Once a file lives on a personal account, you have zero visibility into who’s accessing it, when, and how it’s being shared. This is a nightmare for any international keyword strategy that relies on maintaining a secure, professional brand image.
This is exactly why sticking to a dedicated, secure platform is so non-negotiable. A service built around encrypted file sharing ensures every document stays within a protected environment where security is the default, not an option. For a closer look, our guide on encrypted file sharing explains how this technology keeps your data locked down.
Another critical oversight is failing to clean up access permissions after a project wraps up or a team member moves on. This is especially dangerous when working with offboarded employees or international partners whose contracts have ended.
A shared link without an expiration date is a permanent backdoor to your data. Leaving access open indefinitely is one of the most common yet easily avoidable security mistakes.
Think about it this way: you give a contractor in another country access to a project folder containing localized content. The work gets done, the invoice is paid, but the link to the folder remains active. Months later, that link could be accidentally forwarded or compromised, exposing sensitive files long after the professional relationship is over.
Here’s how to sidestep this common trap:
By correcting these seemingly small habits, you massively strengthen your security posture. It ensures your efforts to share files securely aren’t sabotaged by simple, everyday mistakes, keeping your valuable information safe across your entire collaborative network.

When your company starts operating on a global scale, the security playbook you used before just won’t cut it. Basic measures are a start, but protecting data across different countries means you have to think bigger. You’re dealing with a whole new level of complexity—from shifting regional laws to wildly different tech infrastructures. This demands a robust technical SEO for international reach that includes security as a core component.
Moving past the standard stuff requires a change in how you think. It’s not about just reacting to threats anymore. Instead, you need to proactively build a security framework that’s resilient enough for the long haul. This is non-negotiable for any business looking to grow internationally while keeping customers’ trust and staying compliant.
The absolute cornerstone of modern enterprise security is the Zero-Trust model. It’s built on a simple, yet incredibly effective, principle: never trust, always verify. This approach assumes that a threat could just as easily be inside your network as outside, so every single user and device has to prove who they are before they can touch anything.
For teams spread across the globe, this is a game-changer. With a Zero-Trust mindset, a developer logging in from Berlin goes through the exact same tough verification as an executive in Boston. It completely gets rid of that old, dangerous assumption of “implicit trust” that used to leave so many security holes wide open.
A Zero-Trust security model isn’t about locking people down; it’s about enabling them to collaborate securely. When you verify every single access request, you create a safe space where your global teams can innovate and share ideas with total confidence.
To make your security policies work automatically, you’ll want to lean on Data Loss Prevention (DLP). DLP tools are a lifesaver. They actively scan data that’s leaving your network for sensitive information—like credit card numbers or secret project codes—and can stop a transfer dead in its tracks. This kind of automated oversight is essential for preventing those accidental data leaks that can happen with a global workforce.
You can take this a step further with geo-fencing controls, a powerful tool for geo-targeted landing pages and data management. This technology is exactly what it sounds like: it lets you draw a virtual fence around your data, restricting access based on a user’s real-world location.
Here’s how it works in practice:
These controls are vital for building a secure framework that can handle localized content and international regulations. By being smart about where your data can and can’t go, you align your security strategy with your global business goals. For a deeper dive, our guide on https://blogs.skydrivefolder.com/secure-file-sharing offers more advanced insights. This approach of geo-targeted security also directly helps with conversion optimization per region by building the trust and regulatory alignment that international customers demand.
Even with a great strategy, theory only gets you so far. When you start sharing files securely in your day-to-day work, real-world questions always pop up. Here are some straightforward answers to the things people ask me most often.
Yes, but with one huge catch: you absolutely must be using a service with strong end-to-end encryption. This is non-negotiable.
End-to-end encryption scrambles your data before it leaves your device. This makes it completely unreadable to anyone who might be snooping on that coffee shop or airport Wi-Fi. The file stays locked tight until it reaches the person you sent it to. Before you hit “send” on a public network, always confirm your platform has this feature turned on. It’s your best defense against prying eyes, whether you’re working locally or abroad.
This is a critical distinction, and one that trips a lot of people up. It’s actually pretty simple when you think about it in two stages:
For any project that matters, you need both. You can’t have one without the other and call it secure. End-to-end encryption is the gold standard for protection in transit because not even the service provider can get their hands on your unencrypted files.
For projects with serious security needs, especially those involving international data transfers, a platform offering both encryption at rest and in transit isn’t just a nice-to-have, it’s a requirement. This two-layer approach ensures your data is shielded at every single point in its lifecycle.
Regular access audits are a core part of good security hygiene, especially if you’re working with teams across different countries or bringing on temporary contractors. As a baseline, I recommend a quarterly review for most projects.
However, if you’re dealing with highly confidential information or when a team member leaves the company, you should conduct an audit immediately. Don’t wait. This simple, proactive step ensures only the right people have access to the right data at all times, maintaining compliance across all your operational regions.
Absolutely. Nobody has time for slow transfers, and thankfully, modern secure transfer platforms are built for both speed and scale. They use advanced protocols designed specifically for moving massive assets like 4K video footage or complex architectural models across continents.
Often, these services work by breaking a huge file into smaller, more manageable chunks. This makes the transfer faster and far more reliable, and the file is reassembled automatically on the other side. When you’re picking a service, look for one that specifically mentions support for large files without hitting you with frustrating size caps. You can learn more about how to do this effectively in our guide on how to share large files without giving up speed or security.
Ready to implement these best practices with a platform built for security and ease of use? Sky Drive Folder offers end-to-end encryption, password-protected links, and full control over your shared files. Start sharing securely today.