Address
Australia, Singapore, and USA
Address
Australia, Singapore, and USA

Learn how encrypted document sharing protects your sensitive data. Explore strategies for secure collaboration, compliance, and international data handling.
We've all felt that jolt of anxiety after hitting 'send' on a sensitive document. Did it go to the right person? Is it secure? For businesses operating on a global scale, that worry is magnified. Encrypted document sharing is the answer, transforming digital files from vulnerable data into secure, tamper-proof assets.
Think of it as the difference between a flimsy paper envelope and a high-tech, armored courier box. It's a method that goes beyond basic security, turning readable information into an unreadable code that only the intended recipient, anywhere in the world, can unlock.

Standard ways of sharing files, like attaching a document to a regular email, often leave your data exposed. While convenient, they lack the strength to defend against today's sophisticated cyber threats. To grasp the stakes, it's crucial to understand the common cloud security risks that jeopardize sensitive international data daily.
In our interconnected global economy, data constantly crosses borders, making it a prime target for attackers. Encrypted document sharing has evolved from a "nice-to-have" feature into a non-negotiable component of any successful international keyword strategy. It's foundational for any business aiming to grow its global footprint.
It solves several key problems for global operations:
This security practice is fundamental for businesses reaching multilingual audiences or creating geo-targeted landing pages. When you ask a user in another country to submit their information, you're making an implicit promise to protect it. Encrypted document sharing is how you fulfill that promise, building the trust needed to drive global conversions.
For example, government agencies like Statistics Canada rely heavily on encrypted document sharing as a core tenet of their data privacy framework. They use sophisticated technologies to share and analyze sensitive datasets without ever exposing personal information, proving that top-tier security and useful data can coexist. This approach is crucial for meeting the stringent confidentiality mandates of the Statistics Act.
Ultimately, encrypted document sharing isn't just a feature; it's a critical risk management tool. It builds the digital trust necessary to underpin secure international business strategies and earn credibility in new regions, making it easier to pursue initiatives like backlink building in target regions.
To really get what encrypted document sharing is all about, you first need to understand how the encryption itself works. At its core, encryption is a process that takes your readable document, known as plaintext, and scrambles it into an unreadable format called ciphertext. The only way to unscramble it is with the correct digital key.
Think of it as a secret code. Your file is the original message, and encryption turns it into a jumble of characters that looks like nonsense to anyone who intercepts it.
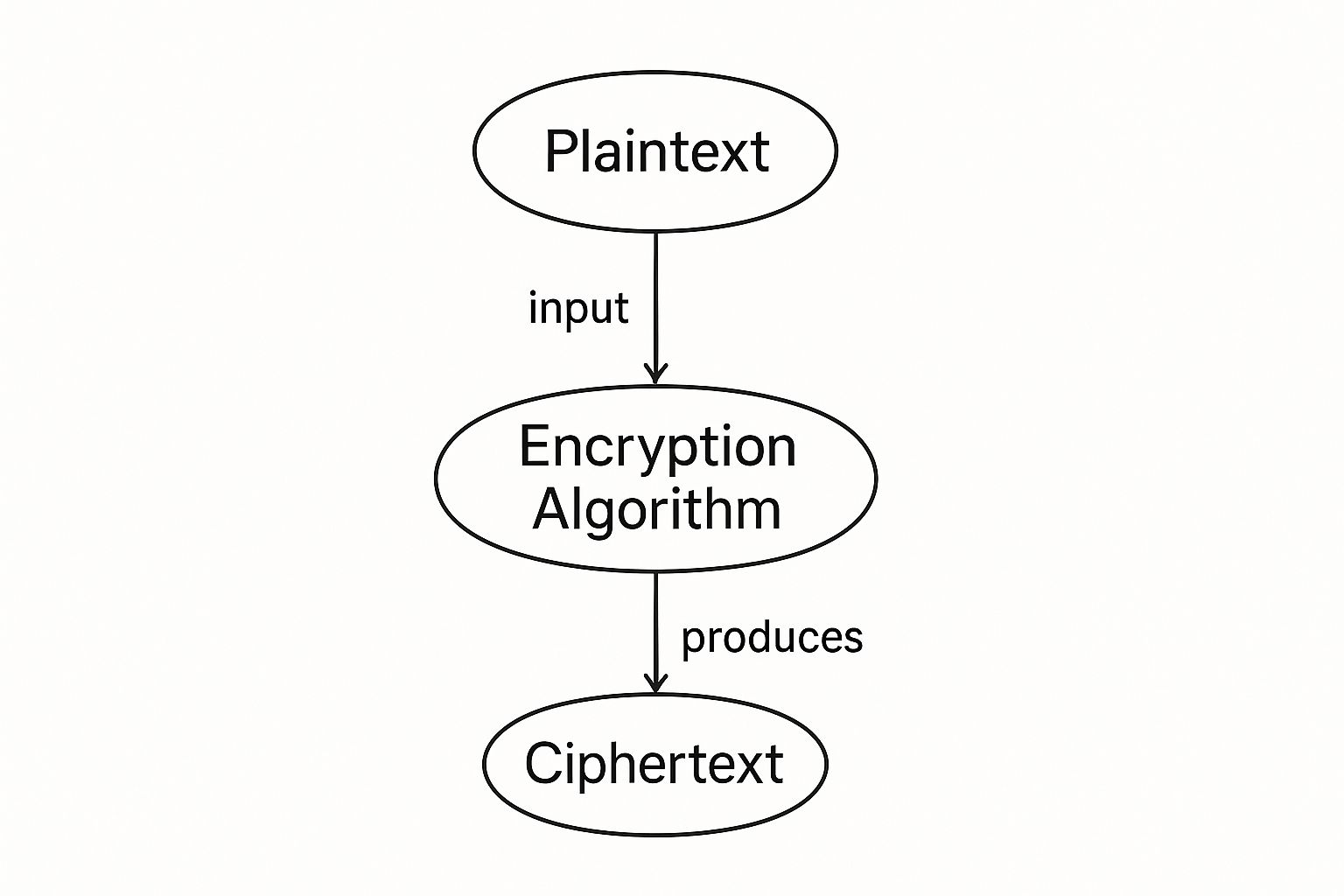
As you can see, a special encryption algorithm—which is just a set of complex mathematical rules—is what does the heavy lifting, transforming your data into something completely unintelligible without the key.
Your files aren't just vulnerable in one place; they face different risks depending on whether they're being sent or just sitting on a server. That's why encryption is designed to protect them at every stage.
Data in Transit: This is your data when it’s on the move. Think about an email zipping across the internet or a file being uploaded to the cloud. Encryption here, often using protocols like SSL/TLS, creates a secure, private tunnel for the data to travel through, shielding it from anyone trying to eavesdrop.
Data at Rest: This is your data when it's stationary—saved on a hard drive, a server, or in a cloud storage platform like Sky Drive Folder. Encrypting data at rest ensures that even if someone physically stole the server or hacked into the storage, the files would be nothing but unreadable gibberish.
A solid security strategy doesn't stop at encryption alone. It's also crucial to understand the broader network security essentials for protecting your digital assets to ensure your files are locked down from every angle.
Not all encryption is created equal. The two main types you’ll run into are symmetric and asymmetric, and the biggest difference between them is how they handle the keys that lock and unlock your data.
Symmetric encryption is like having a single key for your house. The same key locks the door and unlocks it. If you want to give a friend access, you have to find a secure way to give them an exact copy of that key.
Asymmetric encryption works more like a personal mailbox with a mail slot. Anyone can drop a letter (your encrypted file) through the public slot, but only you have the private key to open the mailbox and read what’s inside.
Understanding the difference between these two helps you see what's happening behind the scenes when you share files securely. Industry-standard encryption methods like AES (Advanced Encryption Standard) are a form of symmetric encryption, loved for its incredible speed. In contrast, RSA (Rivest–Shamir–Adleman) is a popular asymmetric method, which is excellent for verifying identities and securely exchanging the secret keys needed for faster symmetric encryption.
This table breaks down the two main types of encryption, showing their key features, common uses, and performance trade-offs to help you understand what protects your data and when.
| Feature | Symmetric Encryption (e.g., AES) | Asymmetric Encryption (e.g., RSA) |
|---|---|---|
| Keys Used | A single, shared key for both encryption and decryption. | A pair of keys: one public (for encrypting) and one private (for decrypting). |
| Speed | Very fast. Ideal for encrypting large amounts of data, like entire hard drives. | Slower. Best suited for encrypting smaller pieces of data, like digital signatures. |
| Key Management | The main challenge is sharing the single key securely with the recipient. | Simpler management. The public key can be shared openly without risk. |
| Best For | Encrypting data at rest (files on a server) and bulk data transfers. | Securely exchanging symmetric keys, creating digital signatures, and verifying identity. |
Ultimately, many secure systems use a combination of both. They'll use the slower asymmetric encryption to safely share a one-time symmetric key, then use that fast symmetric key to encrypt the actual bulk of the data. It's the best of both worlds—unbeatable security and great performance.

It's easy to get lost in the technical jargon of keys and algorithms, but what does encrypted document sharing actually do for your business? At its core, it's your final line of defence. If a breach ever happens and someone gets past your firewalls, properly encrypted files are just unreadable gibberish to them. They're completely useless.
This creates a powerful foundation of trust, especially when you’re working across borders. Imagine you're in the middle of a sensitive merger deal with international partners. Using encrypted sharing means the financial statements, strategic roadmaps, and due diligence reports—valuable content types that drive global conversions—are only ever seen by authorized individuals. It prevents the kind of leak that could derail the entire deal.
Here’s a benefit that’s often overlooked: encryption isn’t just about hiding your data, it’s about making sure it hasn't been secretly changed. This is what we call data integrity. Cryptographic signatures act like a tamper-proof seal, proving that the document you sent is the exact same one the recipient opens.
This is absolutely vital for everything from legal contracts to your company's most valuable intellectual property. When you're sharing proprietary R&D data or product blueprints with a manufacturing partner overseas, you need total certainty that the specifications haven’t been tinkered with along the way.
Encrypted document sharing moves beyond simple access control. It provides mathematical proof that your confidential information remains confidential and, just as importantly, unaltered.
In today's world, a solid encryption strategy is a non-negotiable part of modern risk management and a key element of your overall document management best practices. It’s what gives businesses the confidence to operate on a global scale, whether they're collaborating with international teams or collecting user data through localized content on their websites. To get a broader view of these strategies, it's worth exploring the secure document sharing best practices that industry pros follow.
But the technology alone isn't enough. A truly secure framework also requires clear protocols for your team. This means adopting comprehensive document management best practices that define how files are created, shared, and stored across your entire organisation.
Ultimately, protecting your most valuable digital assets isn't about putting up barriers. It's about creating a secure foundation that supports global growth, builds confidence with your partners, and shields your business from costly data disasters. Security doesn't hinder collaboration; it enables it.
When your business crosses borders, encrypted document sharing stops being a nice-to-have and becomes a non-negotiable part of your legal and international growth strategy. Different countries have their own strict rulebooks for protecting personal data, and ignoring them can lead to eye-watering fines and a permanent stain on your reputation.
If you’re handling information belonging to EU citizens, for example, you’re playing by the General Data Protection Regulation (GDPR) rules. In Canada, the Personal Information Protection and Electronic Documents Act (PIPEDA) is the law of the land. Both of these frameworks require businesses to use strong technical measures to keep personal information safe, with solid encryption being a fundamental expectation.
Using a secure platform designed for this from the ground up helps ensure your data practices are defensible, simplifying your path to global compliance and making your technical SEO for international reach more effective.
For companies trying to land government contracts or operating in heavily regulated spaces like finance or healthcare, meeting certain cryptographic standards isn't just a good idea—it's often a requirement. The one you’ll hear about most is FIPS 140-2 (Federal Information Processing Standard). Think of it as a formal benchmark that proves a system's encryption is genuinely effective.
When a platform achieves FIPS 140-2 validation, it means its cryptographic engine has been put through the wringer and officially approved for high-stakes environments. Checking for this validation when you choose a tool for encrypted document sharing gives you powerful proof that you’re using a solution built for top-tier security.
In Canada, the government is especially clear that any encrypted document sharing solutions used for public and private sector work must meet tough standards like FIPS 140-2. This validation, which was co-developed by Canada's own Communications Security Establishment, sets the bar for software that handles government information, ensuring it’s protected whether it’s sitting on a server or moving across the internet. As more Canadian businesses manage sensitive digital files, using compliant tools is essential for preventing breaches and staying on the right side of laws like the Privacy Act.
At the end of the day, compliance is about more than just avoiding penalties. It’s about building a brand that people anywhere in the world can trust. When your marketing efforts are targeting new regions, your commitment to security speaks louder than any sales pitch. Showing that you protect data with compliant, verified tools becomes a powerful competitive edge and a cornerstone of your conversion optimization per region.
This is especially true in industries with their own unique rules, like healthcare, where regulations like HIPAA in the United States set an even higher standard. Understanding how encryption forms the bedrock of HIPAA-compliant file sharing is crucial for any business in that space. This dedication to security and regulation shows partners and customers everywhere that you take their privacy seriously, paving the way for successful global growth.

Alright, you understand the what and the why. Now for the how. Putting an encrypted document sharing system into practice isn't just about buying software; it's about building a security-first mindset, especially if your teams are scattered across the globe.
Success starts with a couple of non-negotiable demands: end-to-end and zero-knowledge encryption. This powerful combination is your guarantee that only the right people can ever see your files. Not even the service provider can take a peek.
The gold standard for implementation involves a multi-layered approach. You must enforce strong password policies, mandate multi-factor authentication (MFA), and use role-based access controls to limit data exposure based on job function.
These are the foundational pillars that will actually protect your digital assets. For a deeper look at secure methods, you can explore our detailed guide on encrypted file sharing.
When you're working with international teams, security is only half the battle. Performance is just as critical. A key part of your strategy has to be choosing a solution that’s fast and reliable for everyone, no matter where they are. Slow load times will kill adoption before you even get started.
On top of that, you need to think about your people. A platform with multilingual support and localized content capabilities makes a world of difference. When the experience feels familiar and intuitive, teams are far more likely to stick with the secure platform you’ve worked so hard to provide.
By focusing on both tough-as-nails security and a thoughtful international rollout, you can implement a solution that truly protects your data and empowers your global workforce.
Adopting new technology always comes with questions, and it’s smart to get clear answers before making a change. When it comes to encrypted document sharing, one of the biggest worries we hear is whether the extra security will just complicate daily work. Let's tackle some of those common concerns head-on.
Absolutely not. Modern platforms for encrypted document sharing are built with the user in mind. Most are designed to feel just like a standard cloud drive, integrating smoothly into the workflows your team already has down pat.
All the heavy lifting—the complex encryption and decryption—happens automatically in the background. This means your team can share files with top-tier security without needing a technical bone in their bodies, making the whole experience effortless. For a closer look at how this works in practice, you can explore our overview on secure document sharing.
While many popular cloud services do encrypt your files, the real difference is who holds the keys. With most standard services, the provider keeps a copy of the encryption keys, meaning they could technically access your data if they were compelled to.
True end-to-end encrypted platforms, on the other hand, operate on a zero-knowledge principle. This guarantees that only you and your intended recipients hold the keys to unlock your files. The service provider has no way to access your information, which gives you a much higher degree of privacy and control.
This distinction is absolutely vital when you're handling truly confidential information. It ensures your data remains yours and yours alone—a core principle of modern data security.
Ready to experience the confidence that comes with zero-knowledge security? With Sky Drive Folder, you can protect your most sensitive files with powerful, user-friendly encryption. Get started with secure file sharing today.